WordPress is an incredibly popular CMS platform, but because of this popularity, we have seen an uptick in cyber attacks that target WordPress websites. While WordPress’s widespread use makes it a popular target, following secure practices makes it easier to protect against potential vulnerabilities.
In this guide, we will explore specific security practices applicable to both the WordPress backend and the front end to equip you with the knowledge and actionable strategies to protect your content, users, and applications.
By following the advice here, you will be better equipped to deploy and maintain a WordPress website while maintaining the highest security standards for your WordPress projects.
Why You Need to Secure WordPress
A common misconception is that simply using a pre-built CMS will unconditionally protect your website from all attacks. We understand that using a WordPress backend reduces certain risks but doesn’t offer a magic bullet.
If you enable the WordPress API, it becomes a critical attack vector, vulnerable to injection attacks, unauthorized access, and data breaches.
Additionally, using an insecure theme or plugin can provide an easy entry point, requiring its own security measures.
When using an out-of-the-box installation of WordPress, the security challenges are not necessarily eliminated – they are transformed.
Failing to address these new vulnerabilities can jeopardize your data and your users.
11 Ways To Secure Your WordPress CMS
Here are 11 key things that you can do to protect your WordPress environment:
1 – Follow WordPress Security Best Practices
You should follow the fundamental WordPress security practices, such as creating strong, unique passwords for all user accounts and implementing two-factor authentication whenever possible.
In addition to this, you should make sure that you are using a supported version of PHP, as EOL (End of Life) versions of PHP often contain vulnerabilities that are not fixed. You should also make sure that no error logs are displayed to end users.
If an attacker can view your error messages, it will make it easier to launch targeted attacks, which are much more likely to succeed.
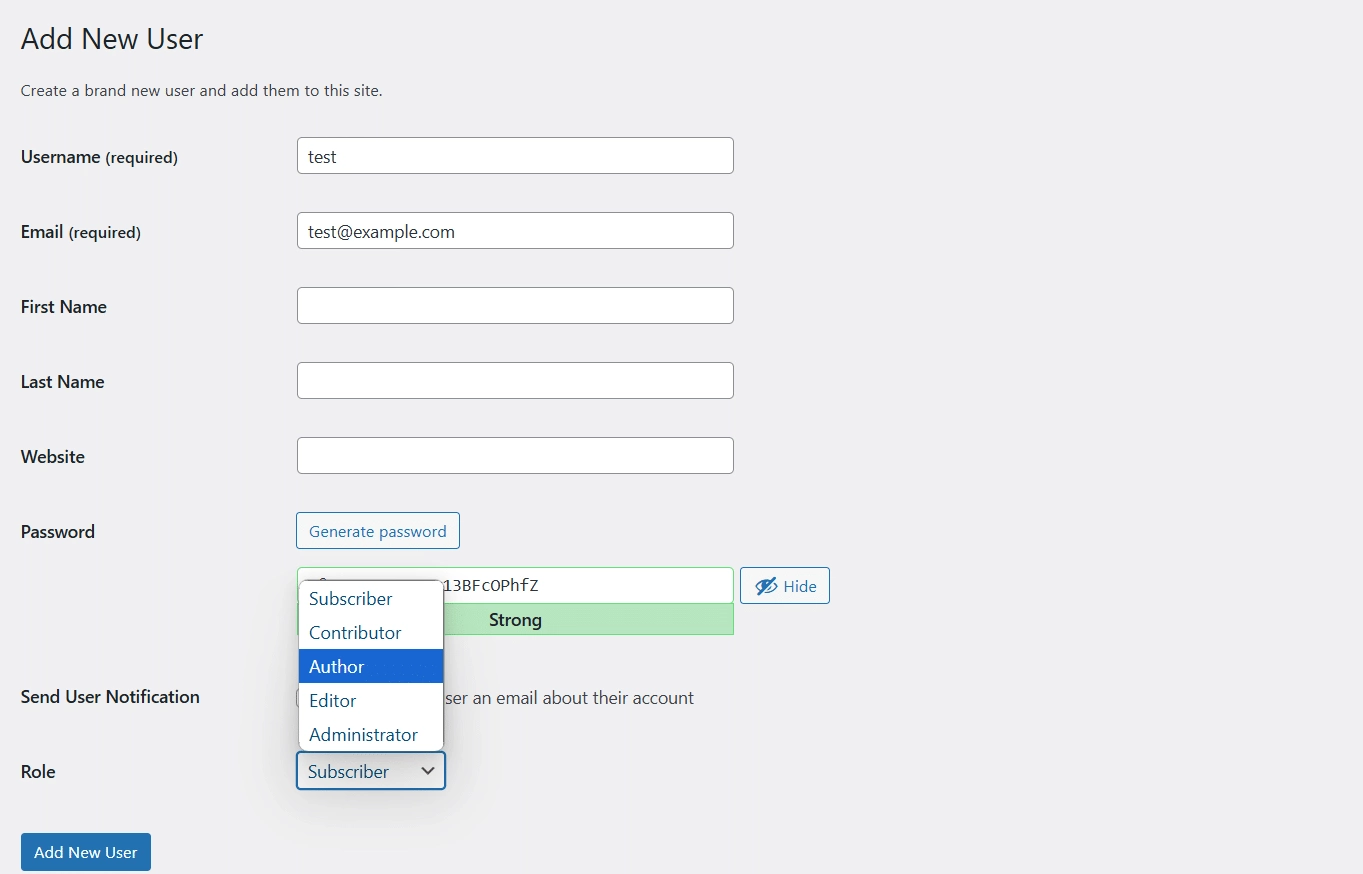
2 – Configure User Roles
If you are working with a team, you should follow the principle of least privilege when assigning user roles in your WordPress dashboard.
This rule states that you should grant users only the minimum permissions necessary for their specific tasks and remove them if they are no longer needed.
You should conduct periodic reviews to check whether all the active accounts still need the permissions granted to them.
You should also create company-wide policies to delete user accounts when a team member leaves the organization to avoid misuse of their credentials.
By minimizing user access, you reduce the potential impact of compromised credentials allowing an attacker to use them for malicious purposes. This also helps to ensure that your WordPress admin area is more secure and that your content is safe.
3 – Secure WordPress Admin Area
Although the default WordPress setup has sensible defaults, you still need to secure its WordPress admin area. If an attacker gains access to your WordPress admin account, they will have unrestricted access to your website.
Therefore, you should restrict access to the WordPress admin dashboard using IP whitelisting or other access control measures.
You should also change the default admin login path to something less obvious. This will discourage attackers and most automated bots from attempting to access the admin dashboard.
4 – Protect Your Site from Plugin Vulnerabilities
WordPress is extremely popular because plugins allow you to easily extend its functionality.
However, if your website is not managed correctly, each additional plugin or theme increases the chances that one of them will have a vulnerability that could then subsequently be exploited to gain access to your site.
Simply put: You should be vigilant about the plugins you install in WordPress, and install plugins only from reputable sources.
Furthermore, you should update all your plugins and apply security patches to reduce the risk of getting hacked.
Managing and tracking vulnerabilities for each plugin can be tedious if you have multiple WordPress websites. To stay ahead of attackers, you can use Patchstack to track vulnerabilities in up to 10 websites and get a 48-hour early warning about security vulnerabilities.
5 – Protect Your Configuration Files
WordPress uses a wp-config.php file to store its database credentials and other important information. You should protect this file as it contains sensitive information that can be used to access your website’s information.
A good way to protect your wp-config file is to restrict read-write access to your file system. Usually, a permission level of 600 or stricter is considered safe, as it prevents other users on the same computer from editing or executing this file.
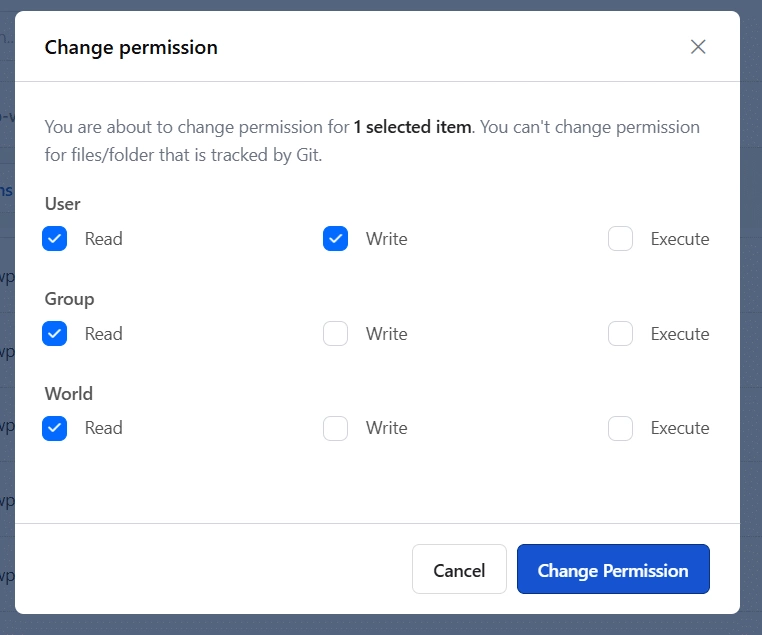
You can also move this file out of your website’s public path because, by default, WordPress searches for the wp-config file in its current directory, and if it is not found, it looks for it in the parent directory.
Moving your wp-config file to the parent directory will make it even more difficult for attackers to access it.
To enhance your design skills, check out our video tutorial on Creating a WordPress Website Footer with Gutenberg Blocks.
6 – Data Validation & Sanitization
Many WordPress developers build or edit their own WordPress plugins and themes to customize their websites and add additional functionality.
If you are building a custom solution, you should implement robust validation at every entry point where users can submit data. You can validate form inputs immediately in the browser using JavaScript to catch obvious issues before the data reaches the server.
For example, check that email addresses follow the correct format and that the required fields aren’t empty.
On the server side, you should never trust incoming data, even from authenticated users. WordPress provides built-in functions such as sanitize_text_field() and wp_kses() that you can use to clean user input before saving it to the database.
These functions strip out potentially harmful HTML tags and JavaScript while preserving legitimate content.
When displaying data back to users, you can protect against cross-site scripting (XSS) attacks by properly escaping output using functions such as esc_html() and esc_url().
Modern JavaScript frameworks, such as React, handle much of this automatically, but we must still be vigilant about properly encoding dynamic content.
Similarly, you can validate incoming requests using WordPress’s register_rest_field() sanitization callbacks for REST API endpoints.
7 – Implement Security Headers
Security headers are additional information sent from the server to the client’s browser along with every web request. These headers instruct the browser to process and display this content to users.
When configuring your server instance, you should implement security headers such as Content-Security-Policy (CSP) to restrict which resources browsers can load – this effectively prevents many injection attacks.
A well-configured CSP provides granular control over trusted sources for scripts, styles, images, and other resources.
Similarly, the X-Frame-Options header stops clickjacking attempts by controlling how pages can be embedded in iframes. At the same time, HTTP Strict Transport Security (HSTS) forces encrypted HTTPS connections to protect data in transit.
You can audit your security headers using tools such as SecurityHeaders.com to verify they are correctly configured.
8 – Preventing XSS (Cross-Site Scripting) Attacks
If you are building your WordPress theme or extending the functionality of an existing theme by creating a child theme, then you can consider using one of the many new and modern frameworks and technologies available in the market.
Most modern frameworks are developed with security in mind. They provide built-in XSS protection by automatically escaping dynamic content. For example, React escapes values embedded in JSX, while Vue.js sanitizes template inputs.
However, you should be cautious when using dangerous functions like dangerouslySetInnerHTML in React or v-html in Vue, as these bypass built-in protections and require careful manual sanitization.
If you are using these functions, creating custom tests to test the webpage by sending an XSS payload is a good idea.
9 – Protecting Against CSRF (Cross-Site Request Forgery) Attacks
A Cross-Site Request Forgery attack exploits authenticated user sessions to perform unauthorized actions in the user’s browser.
In WordPress, you can prevent CSRF attacks by implementing the double submit cookie pattern, where a CSRF token is included in a secure cookie and either requests headers or form fields.
Before processing sensitive requests, you can validate that these tokens match.
You can also use the SameSite cookie, which provides additional CSRF protection by controlling when browsers send cookies to third-party sites. You can set authentication cookies with SameSite=Strict to ensure they only get sent in first-party contexts.
10 – Keep Your Secrets Secret
If you are using a popular WordPress page builder such as Elementor or Gutenberg, you might think that security concepts like “secret management” are only for advanced developers. That’s a common but dangerous misconception.
Your website’s security depends on protecting all sensitive information, not just your WordPress admin password.
Your managed WordPress hosting provider likely gives you database credentials, maybe even SSH login details or SSH keys. You need to treat these as top-secret information. Someone could gain complete control of your website and data if these details leak.
If you’re using any WordPress APIs, you probably have API keys. You must keep these keys secret, too.
It might be tempting to paste these keys directly into your theme files, a custom plugin, or even your page builder’s custom code sections – but don’t do it. Hardcoding secrets is like leaving your house keys under the doormat.
Instead of hardcoding, you should use secure methods for storing sensitive information. Your hosting provider might offer built-in tools for managing these secrets, so check their control panel or documentation.
If you’re more technically inclined, explore using environment variables or secrets managers from cloud providers.
Learn about user management by watching How to Add Custom ACF Fields on the WordPress Signup Registration Form.
11 – Protect the Server Infrastructure
Your WordPress site’s security isn’t just about WordPress itself – it’s also about the server it lives on. Even if you’ve hardened WordPress, an insecure server is a wide-open door for attackers. Think of it like having a strong lock on your front door but leaving your windows wide open. You must secure the entire “house”, not just the front entrance.
If you’re using a managed WordPress hosting provider, you probably don’t need to configure every aspect of your server security. However, you should still choose a provider with a strong reputation for security.
We recommend using modern WordPress hosting providers like Servebolt, which offer features such as Accelerated Domains. This can actively block malicious traffic before it even reaches your server and provide an extra layer of defense without adding additional burden to your server.
On the other hand, if you’re managing your server (for example, on a cloud provider like AWS, Google Cloud, or DigitalOcean), you have a much bigger responsibility.
You should install and configure a firewall to control incoming traffic, only allowing access to necessary services and trusted IP addresses.
Suggested: Want to keep your WordPress site safe? Learn how to block unwanted visitors with this simple video!
This is an important step that requires technical knowledge, and if you are not sure how to do this properly, you should hire a professional server administrator.
Whether you’re self-hosting or using a basic, unmanaged VPS, you must secure SSH access. You should disable password-based logins entirely and use SSH key-based authentication instead.
This is significantly more secure and prevents brute-force attacks on your server’s login. Additionally, you should limit SSH access to specific, trusted users by carefully managing your authorized_keys file.
If you’re comfortable with advanced server administration and networking, consider implementing a three-tier architecture. This separates your web, application, and database server, adding extra isolation layers.
You can also implement rate limiting at multiple levels – your web server, application, and any APIs – to prevent attackers from overwhelming your server with requests (DDoS attacks) or trying to guess passwords (brute-force attacks).
Stay updated with Helpful WordPress Tips, Insider Insights, and Exclusive Updates – Subscribe now to keep up with Everything Happening on WordPress!
Key Takeaways
In this guide, we have discussed how WordPress faces unique security challenges and explained the importance of a layered security strategy, from fundamental WordPress hardening to limiting user access controls by implementing the principle of least privilege.
Shifting to a WordPress CMS can still leave open some attack vectors, such as API vulnerabilities and frontend exploits. Therefore, you must enable additional security measures like strong authentication, robust data validation, and regular dependency management.
Ready to take your WordPress site to the next level? Explore Nexter’s Getting Started Docs to start building with our builder components.
You can also find many video tutorials regarding security, such as How to Add Google reCAPTCHA to WordPress Login/Registration for spam protection and how to improve email functionality with How to Fix WordPress Email Not Sending Issue.
Finally, don’t forget to explore our resources on Nexter Blocks and Nexter Extensions while keeping your site fast and secure!Join the NexterWP community today and become a WordPress pro!